MFA Operator Configuration
Exploring
This program lets administrators configure Multi-Factor Authentication per operator.
Things you can do in this program include:
-
Enable Multi-Factor Authentication for an operator that has not yet been configured for MFA
- Disable Multi-Factor Authentication for an operator that is currently configured for MFA
- Suspend Multi-Factor Authentication for an operator that is currently configured for MFA
- Resume Multi-Factor Authentication for an operator that is currently suspended
This program is accessed from the Program List of the SYSPRO menu:
- Program List > Administration > Setup
Multi-Factor Authentication (MFA) is the process of identifying a user by validating two or more methods of authentication from independent credential categories. This authentication method ensures that a user is only granted access after successfully presenting two or more pieces of evidence to an authentication mechanism.
The three most commonly used authentication factors are:
-
Knowledge: something only the user knows (e.g. a user name and password, a PIN or answers to security questions).
-
Possession: something the user has (e.g. a smart-phone, Time-based One-time Password (TOTP) or smart card).
-
Inherence (or biometrics): something unique that proves the user's identity (e.g. a fingerprint, iris scan or voice recognition).
The principle of Multi-Factor Authentication is that there is no perfect authentication factor. Any one factor that is implemented will have its strengths and weaknesses. For this reason, the concept of Multi-Factor Authentication is that a second or third factor compensates for the weakness of the other factors and vice-versa.
The Time-based One-Time Password algorithm (TOTP) is an extension of the HMAC-based One-Time Password algorithm (HOTP) which generates a unique one-time password based on the current time.
It has been adopted as Internet Engineering Task Force standard RFC 6238, is the cornerstone of Initiative For Open Authentication (OATH), and is used in a number of two-factor authentication systems.
The one-time password must validate over a range of times between the authenticator and the authenticated because of latency (both network and human) and unsynchronized clocks.
Both the authenticator and the authenticatee compute the TOTP value, then the authenticator checks if the TOTP value supplied by the authenticated matches the locally-generated TOTP value.
Some authenticators allow values that should have been generated before or after the current time in order to account for slight clock skews, network latency and user delays.
Starting
You restrict operator access to activities within a program using the Operator Maintenance program.
You can restrict operator access to the fields within a program (configured using the Operator Maintenance program).
You can restrict access to the eSignature transactions within a program at operator, group, role or company level (configured using the Electronic Signature Configuration Setup program). Electronic Signatures provide security access, transaction logging and event triggering that gives you greater control over your system changes.
You can restrict operator access to programs by assigning them to groups and applying access control against the group (configured using the Operator Groups program).
You can restrict operator access to functions within a program using passwords (configured using the Password Definition program). When defined, the password must be entered before you can access the function.
The following configuration options in SYSPRO may affect processing within this program or feature, including whether certain fields and options are accessible.
The Setup Options program lets you configure how SYSPRO behaves across all modules. These settings can affect processing within this program.
Setup Options > System Setup > Login
-
Multi-factor authentication
- Multi-factor authentication required
- User applicability
-
Multi-factor authentication methods
- Email authentication required
- Operator can set own email address
- Email must match pattern
- Google authenticator required
Setup Options > System Setup > Connectivity
- SMTP server IP address
- Outgoing email address
- Username
- Password
- Server port
- Use SSL
-
Multi-Factor Authentication is not currently available for the following (i.e. an operator configured for Multi-Factor Authentication won't be able to login to these platforms):
-
SYSPRO Supply Chain Portal
-
SYSPRO Espresso
-
-
SYSPRO operators cannot be enabled for simultaneous use of Multi-Factor Authentication and:
- SSO using Active Directory (i.e. the operator is defined as an Active Directory user)
- Concurrent usage (i.e. the Allow concurrent use of this operator option is enabled against the operator in the Operator Maintenance program)
Solving
The simultaneous usage of concurrent access and Multi-Factor Authentication is not possible.
This message is therefore displayed if you attempt to enable Multi-Factor Authentication for an operator that is currently defined to use concurrent logins.
To enable Multi-Factor Authentication against this operator you must disable the Allow concurrent use of this operator option in the Operator Maintenance program, before enabling MFA in the MFA Operator Configuration program.
The following auditing and logging capabilities are available to ensure that Multi-Factor Authentication is managed and tracked correctly:
The system automatically records when Multi-Factor Authentication is enabled, disabled, suspended or resumed for an operator using the MFA Operator Configuration program.
These entries are stored in the AdmMfaAuthEnabled table and you can use the System Audit Query program to view the history.
This table includes which operator changed the authentication status and the operator that was changed.
The system automatically tracks each operator's configured authentication method when they use the Multi-Factor Authentication Setup program.
These entries are stored in the AdmMfaAuthConfig table.
This program lets you view the history of successful MFA authentications for the company.
SYSPRO automatically tracks each time an operator successfully authenticates themselves to SYSPRO through Multi-Factor Authentication and logs which authentication method is used. Its purpose is to assist system administrators in effectively managing system security.
The entries are stored in the AdmMfaAuthHistory table which records each time an operator successfully logs into SYSPRO using Multi-Factor Authentication. It includes the date and time they were prompted for the additional authentication, as well as the method used to login and the computer name from which this was done. The MFA Operator History Query program lets you view the history.
Although failed login attempts are not currently logged, this will be addressed in a later software release.
When you login as an operator requiring Multi-Factor Authentication, the following rules apply to the AdmOperator table of your system-wide database:
-
The AuthenticationType entry must be M (indicating multi-factor authentication).
-
The OperatorType entry must be N (indicating normal operator).
-
The OperatorStatus entry must be A (indicating active).
-
The operator code cannot be prefixed with underscores (e.g. __BOT)
-
The operator cannot be locked out (i.e. the OperatorLockedOut entry must contain spaces and not an L entry).
An operator code that is configured for Multi-Factor Authentication can't be used to access applications that use e.net.
When disabling Multi-Factor Authentication for an operator, all the MFA-configured information is removed; only the history is retained.
Operators who are disabled for MFA revert to entering the traditional user name and password to access SYSPRO.
Disabling MFA for an operator is useful when that operator no longer requires an additional authentication method to access SYSPRO.
When suspending Multi-Factor Authentication for an operator, the additional authentication is effectively paused; all the MFA-configured information and history is retained.
Operators who are suspended for MFA revert to entering the traditional user name and password to access SYSPRO.
Suspending MFA for an operator is useful when that operator requires temporary suspension from the additional authentication requirement.
For example:
If an operator is configured to use Google authentication and they lose their phone, they can't access SYSPRO to configure or validate another method. Suspending their MFA allows them to do this.
Service operators are created by SYSPRO and are used by SYSPRO services to obtain information about SYSPRO.
The service operator code starts with a double underscore to differentiate them from other operators. A default company code must be assigned to each service operator within the Operator Maintenance program, as we use the company code to log in the service operator via e.net .
The following is a list of service operators and their function within SYSPRO:
-
The __ADSYNC service operator is used by the SYSPRO 8 Active Directory Sync Service to push Microsoft Active Directory (AD) information into SYSPRO for Active Directory managed operators.
-
The __DFM service operator is used by the SYSPRO 8 Document Flow Manager Folder Poller and SYSPRO 8 Document Flow Manager Queue Poller to monitor folders, send files to the queue and process files.
-
The __ESP service operator is used by the following services:
-
SYSPRO 8 Espresso Service,
-
SYSPRO 8 Espresso Notification Service,
-
SYSPRO Espresso Development Plugin and the
- SYSPRO Avanti Web Service to obtain information for the password reset and forgot password functionality.
-
-
The __POS service operator is used by the SYSPRO 8 Point of Sale Services to determine and validate the setup options and required credentials at start up, update the required databases and post to SYSPRO (if the Point of Sale operator doesn't have access to SYSPRO).
-
The __RUL service operator is used by the SYSPRO 8 Rules Engine Service and the SYSPRO 8 Rules Data Service.
-
The __SA service operator is used by the SYSPRO 8 Analytics service to make business object calls.
-
The __SAI service operator is used by the SYSPRO 8 Machine Learning service.
-
The __SRS service operator is used by the SYSPRO 8 Reporting Host Service and the SYSPRO 8 Cognitive Service to manage client-side report printing.
-
Only specific services use service operators to log in via e.net.
-
SYSPRO creates service operators by copying the ADMIN operator. If the ADMIN operator record doesn't exist (i.e. it may have been deleted), then the current operator is used when saving system details from the Setup Options program.
Using
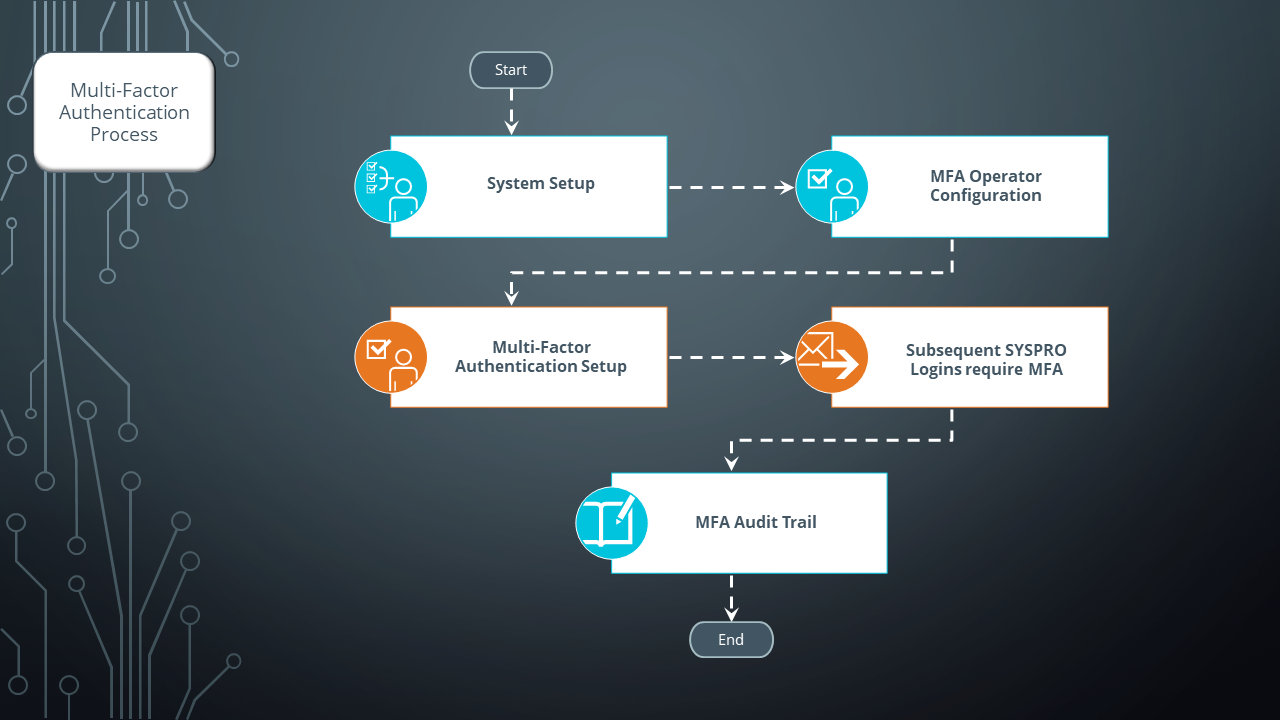
The following describes how a system administrator configures Multi-Factor Authentication in SYSPRO:
-
From the Login System Setup pane within the System Setup category of the Setup Options program, indicate that Multi-Factor Authentication is required against all, or specific operators.
-
Use the MFA Operator Configuration program to view and configure additional MFA requirements (e.g. enabling, disabling, suspending or resuming an operator's MFA requirement).
-
Once MFA is enabled for operators, they are automatically prompted by the Multi-Factor Authentication Setup program when next they login to SYSPRO.
Operators use this program to configure and validate their preferred authentication method.
-
Each subsequent login to SYSPRO requires the one-time, time-based pin from the configured MFA method, before the operator's login is validated.
-
Use the System Audit Query program to review an audit log of all operators enabled for Multi-Factor Authentication.
- Columns in a listview are sometimes hidden by default. You can reinstate them using the Field Chooser option from the context-sensitive menu (displayed by right-clicking a header column header in the listview). Select and drag the required column to a position in the listview header.
- Press Ctrl+F1 within a listview or form to view a complete list of functions available.
Referencing
| Field | Description |
|---|---|
|
Enable MFA |
After selecting the applicable operators from the Operators pane, this function enables them for Multi-Factor Authentication. Operators who are enabled for MFA need to use an additional form of authentication (over-and-above the traditional user name and password) when accessing SYSPRO. |
|
Disable MFA |
After selecting the MFA enabled operators within the Operators pane, this function disables their Multi-Factor Authentication requirement. Operators who are disabled for MFA revert to entering the traditional user name and password to access SYSPRO. Disabling MFA for an operator is useful when that operator no longer requires an additional authentication method to access SYSPRO. |
| Suspend MFA |
After selecting the MFA enabled operators within the Operators pane, this function suspends their Multi-Factor Authentication. Operators who are suspended for MFA revert to entering the traditional user name and password to access SYSPRO. Suspending MFA for an operator is useful when that operator requires temporary suspension from the additional authentication requirement. For example: If an operator is configured to use Google authentication and they lose their phone, they can't access SYSPRO to configure or validate another method. Suspending their MFA allows them to do this. |
| Resume MFA |
After selecting a suspended operator within the Operators pane, this function reinstates their requirement for Multi-Factor Authentication. Once MFA is resumed, the operator is required to use their user name, password and an additional form of authentication when accessing SYSPRO. |
| Field | Description |
|---|---|
| Select |
Use the checkbox in this column to select multiple operators for actioning. This is only required when using the following toolbar options:
|
| Operator |
This indicates the operator code. |
| Name |
This indicates the name of the operator. |
| Enable action |
Use the Enable or Disable functions within this column to enable or disable Multi-Factor Authentication for the selected operator. Operators who are enabled for MFA need to use an additional form of authentication (over-and-above the traditional user name and password) when accessing SYSPRO. Operators who are disabled for MFA revert to entering the traditional user name and password to access SYSPRO. Disabling MFA for an operator is useful when that operator no longer requires an additional authentication method to access SYSPRO. |
| Suspend action |
Use the Suspend or Resume functions within this column to suspend or resume Multi-Factor Authentication for the selected operator. Operators who are suspended for MFA revert to entering the traditional user name and password to access SYSPRO. Suspending MFA for an operator is useful when that operator requires temporary suspension from the additional authentication requirement. For example: If an operator is configured to use Google authentication and they lose their phone, they can't access SYSPRO to configure or validate another method. Suspending their MFA allows them to do this. Once MFA is resumed, the operator is required to use their user name, password and an additional form of authentication when accessing SYSPRO. |
| MFA Status |
This indicates the current MFA status for the operator. |
| Auth status code |
This is an internal code used to indicate the MFA Status. |
| Status |
This indicates the current status of the operator (as recorded in the OperatorStatus column of the AdmOperator table of your SYSPRO database): The operator is active in SYSPRO and Microsoft Active Directory (AD) and can log into SYSPRO. The operator is disabled from one of the following and can't log into SYSPRO or the SYSPRO Supply Chain Portal:
The operator was either removed via Microsoft Active Directory (AD) or the Portal User Management program and can't log into SYSPRO or the SYSPRO Supply Chain Portal. |
|
If the operator is MFA enabled, this column indicates the email address configured against the operator's email authentication method. |
|
| Email override |
This indicates whether the operator is allowed to override the authentication email address when configuring and verifying their MFA authentication in the Multi-Factor Authentication Setup program. This is configured at the Operator can set own email address option within the Email configuration of the Multi-Factor Authentication pane. |
| Override email address |
This is only relevant if the Operator can set own email address option is enabled within the Email configuration of the Multi-Factor Authentication pane. This indicates the email address entered by the operator in the Multi-Factor Authentication Setup program when they configured and validated their email authentication method. |
|
Auth type code/Authentication type |
This indicates the authentication type used to log into SYSPRO. A SYSPRO password is required for the operator when logging into SYSPRO.
Multi-Factor Authentication is enabled for the operator. When logging into SYSPRO, the operator code, password and additional authentication method is required. You can't enable Multi-Factor Authentication for an operator that is defined for concurrent access (i.e. the Allow concurrent use of this operator option is enabled against the operator). SSO using Active Directory is enabled for the operator. Microsoft Windows authentication is used when logging into SYSPRO. Because an operator's Microsoft Active Directory (AD) credentials are used to log into SYSPRO, they are not prompted for an operator code or password at the SYSPRO login dialog. SSO Identity Provider Integration is enabled for the operator and authentication via one of the following identity providers is required when logging into SYSPRO:
Because an operator's SSO Identity Provider Integration credentials are used to log into SYSPRO, they are not prompted for an operator code or password at the SYSPRO login dialog. |
| CMS only user |
This indicates whether the operator is only enabled to use the Contact Management System. |
| Currently logged in |
This indicates whether the operator is currently logged into SYSPRO. |
| Date operator added |
This indicates the date on which the operator was created in SYSPRO. |
| Date operator changed |
This indicates the date that the Status of the operator was last changed. |
| Default method |
This indicates the operator's preferred method of authentication. |
| Espresso user |
This indicates whether the operator is a SYSPRO Espresso user. |
|
Last login/Last login date/Last login time |
This indicates the date and time that the operator code was last used to load SYSPRO. |
| Location |
This indicates the physical location of the operator. |
| Locked out |
This indicates whether a lock has been set against the operator (i.e. when locked out, the operator is unable to load SYSPRO). |
| Operator reason |
This indicates the reason why the operator is locked out. |
| Operator type |
This indicates the operator type (as recorded in the AdmOperator table): This is a standard operator that can access the following SYSPRO platforms:
This is a template operator record that can be used as a baseline configuration to simplify the creation of operators in similar areas or departments. For example: You can create a template for operators in the Accounts department that contains all the general configuration for those type of operators. Then in future, when creating an operator code for someone in accounts, you can use this template to simplify the process. A template operator can't log into SYSPRO. Template operators are required when creating portal users in the Portal User Management program. The following fields can't be changed for Template operators:
This is a named user that is only used for the SYSPRO Supply Chain Portal. Portal users are created using the Portal User Management program and can log into the following SYSPRO platforms:
The following fields can't be changed for Portal operators:
You also can't copy a Portal user/operator. This is an operator managed by Microsoft Active Directory (AD) (via the SYSPRO 8 Active Directory Sync Service). AD Managed users are created using the Active Directory User Management program and can access the following SYSPRO platforms:
The following fields can't be changed for AD Managed operators:
This is an operator managed by SSO Identity Provider Integration. SSO with ID Integration users are managed using the Single Sign-On Operator Configuration program and can access the following SYSPRO platforms:
|
| POS only user |
This indicates whether the operator is only enabled for SYSPRO Point of Sale. |
|
Primary group/Primary group code |
This indicates the primary operator group to which this operator belongs. |
|
Primary role/Primary role code |
This indicates the role descriptor usually matching the job description or job function assigned to an operator. |
This pane displays all operators that are currently configured for Multi-Factor Authentication. The entries are grouped by operator and reflect all authentication methods configured.
| Field | Description |
|---|---|
| Authentication method |
This indicates the operator's method of authentication. |
| Authentication validated |
This indicates if the authentication method has been validated in the Multi-Factor Authentication Setup program. |
|
Date first validated/Time first validated |
This indicates when the operator first validated the authentication method Multi-Factor Authentication Setup program. |
|
Date last validated/Time last validated |
This indicates when the operator last validated the authentication method Multi-Factor Authentication Setup program. |
Copyright © 2025 SYSPRO PTY Ltd.