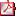Security Settings Dashboard

Configuring security and ensuring consistency across various operators is a complex process that typically involves a number of programs.
SYSPRO's Security Settings Dashboard program lets SYSPRO administrators query operator security settings within a single program.
Exploring
Things you can do in this program include:
-
Query and view security information.
-
Verify which operators have access (and how the access is configured) to various securable entities.
-
View possible program conflicts.
-
Amend security configuration in related programs via smart links.
Starting
You can restrict operator access to programs by assigning them to groups and applying access control against the group (configured using the Operator Groups program).
-
Because the access control settings for the elements listed below are all displayed using a single list view, we don't recommend you customize this control (e.g. adding custom columns relating to master data):
-
Warehouses
- AR Branches
- AP Branches
- Banks
- Job classifications
-
Account types
- Contact properties
- Contact classes
- Contact types
- Contact categories
- Contact territories
-
Solving
A program conflict is where permission is assigned to an operator for two or more programs which could potentially constitute a role or task conflict in your organization.
For example:
If access to the AP Invoice Posting and Payment Cycle Maintenance programs should never be granted to the same operator, then these programs must be listed as a pair in the Conflict.txt file (residing in the \Work folder).
If an operator is subsequently granted access to both programs, a conflict is highlighted by the system.
The dashboard displays all permissions configured for all access combinations.
For example:
If an operator has five roles and four of them have access to a program, then four entries will be shown in the operator list - each with different configuration sources.
Security access information is built using a SQL script (Dashboard_SSet_Info.SQL) at the time of loading the program or selecting the Refresh button.
The total figure in the Securables pane is sometimes more than the total number of entities because a single operator could have access defined across multiple roles.
For example:
A single operator could have five roles, but only four of the roles have access. This will add four to the total instead of just the one.
Within the Security Settings Dashboard the count of users currently logged in is obtained from the operator table (AdmOperator) which indicates whether an operator is logged in (identified by the flag LoggedInStatus).
This flag is updated when a user logs out of SYSPRO in a controlled manner. However, the flag remains unchanged if a user disconnects due to an issue,such as a client server failure.
The list of users displayed in the View Users program works slightly differently as it reads in the individual entries directly from the AdmCurrentUsers table.
Using
-
Columns in a list view are sometimes hidden by default. You can reinstate them using the Field Chooser option from the context-sensitive menu (displayed by right-clicking a header column header in the list view). Select and drag the required column to a position in the list view header.
-
Fields on a pane are sometimes removed by default. You can reinstate them using the Field Selector option from the context-sensitive menu (displayed by right-clicking any field in the pane). Select and drag the required fields onto the pane.
The captions for fields are also sometimes hidden. You can select the Show Captions option from the context-sensitive menu to see a list of them. Click on the relevant caption to reinstate it to the form.
If the Show Captions option is grayed out, it means no captions are hidden for that form.
-
Use the smart links provided in the dashboard to instantly access the related program where security is configured.
For example:
Using the smart link provided in the Operators list, you can query and maintain security settings for an operator directly in the Operator Maintenance program.
-
To refresh the information displayed in the dashboard, select the Refresh button from the program toolbar.
This is useful if you have changed any security configuration while the dashboard is open.
Referencing
|
Column |
Description |
|---|---|
|
Securable |
This indicates all entities that can be secured within each of your SYSPRO companies. As you select each securable, the subsequent detail of that entity is populated in the adjacent Report Control pane. These lists (by default) are grouped by module and remain static for all companies. Securables include:
|
|
Level |
This indicates the level or method according to which the entities can be secured. |
|
Total |
This indicates the number of each entity that can be secured. |
|
Secured |
This indicates the number of entities that are specifically secured. |
Configured security information for SYSPRO is displayed here.
| Field | Description |
|---|---|
|
Operator summary information |
|
|
Total operators defined |
This indicates the total number of operators defined in your system. |
|
Currently logged in |
This indicates the number of operators currently logged in. |
|
Administrators |
This indicates the number of operators belonging to a primary group that is set as an administrator group. |
|
CMS Only |
This indicates the number of operators defined as CMS-only users. |
|
POS Only |
This indicates the number of operators defined as POS-only users. |
|
Espresso Only |
This indicates the number of operators defined as Espresso-only users. |
|
No password set |
This indicates the number of operators who do not have a password defined. |
|
No password expiry |
This indicates the number of operators whose passwords do not expire. |
|
Active |
This indicates the number of operators who have logged in during the last 30 days. |
|
Inactive |
This indicates the number of operators who have not logged in during the last 30 days. |
|
Never logged in |
This indicates the number of operators who have never logged into SYSPRO. |
|
No primary role defined |
This indicates the number of operators who do not have a primary role defined. |
|
Role summary information |
|
|
Total roles defined |
This indicates the number of all roles defined in your system. |
|
Primary role |
This indicates the number of roles that have been defined as a primary role against an operator. |
|
Secondary role |
This indicates the number of roles only defined as a secondary role against an operator. |
|
Program access |
This indicates the number of roles configured to control program access. |
|
Activity and field access |
This indicates the number of roles configured to control activity and field access. |
|
Access control |
This indicates the number of roles configured to control access to entities such as warehouses. |
|
Electronic signatures |
This indicates the number of roles configured for electronic signatures. |
|
Not used |
This indicates the number of roles that have been configured but are not yet associated with any operators. |
|
Group summary information |
|
|
Total groups defined |
This indicates the number of all groups defined in your system. |
|
Administrator |
This indicates the number of groups configured as administrator. |
|
Can logout users |
This indicates the number of groups that have the ability to log out users from the system. |
|
Primary groups |
This indicates the number of groups defined as primary groups against operators. |
|
Sub groups |
This indicates the number of groups used as secondary groups against operators. |
|
Not used |
This indicates the number of groups not associated to operators in any way. |
|
License setup information |
This grouping of information displays standard information regarding your SYSPRO licenses. |
|
Password options |
This grouping of information displays the password options configured within the System Setup program. |
|
Password rules |
This grouping of information displays the password rules configured within the System Setup program. |
| Field | Description |
|---|---|
|
Company information |
This grouping of information displays general information for the company selected in the Securable list. |
|
Access information |
This grouping of information provides an overview of how security is configured for the selected company. |
|
Operators with access to company |
This indicates the number of operators defined with access to the company (i.e. users who can log on). |
|
Program access |
This indicates how program access is controlled in this company:
|
|
Activities and fields |
This iIndicates how access to activities and fields is controlled in this company:
|
|
Access control |
This iIndicates how access control (e.g. the ability to allow or deny access to one or more certain fields) has been configured for this company:
|
|
Electronic signatures |
This indicates how electronic signatures are configured for the company selected:
|
| Column | Description |
|---|---|
| Program | This indicates the program entity. |
| Description | This indicates the program name. |
| E.Net | This indicates whether the program is a business object for e.net. |
| Custom | This indicates whether the program is a third party custom program. |
| Company | This indicates the company. |
| Potential conflicts |
When you select the programs securable, any conflicts found in the CONFLICT.TXT file residing in the \Work folder are loaded and indicated here. |
| Sequence |
This indicates the sequence in which the programs have been defined in the flat files IMPPRG.IMP and CUSPRG.IMP. |
| Column | Description |
|---|---|
| Description | This indicates the activity name. |
| E.Net | This indicates whether the activity is applicable for a business object for e.net. |
| Custom | This indicates whether the activity is a third party custom program. |
| Company | This indicates the company. |
| Number | This indicates the activity number as defined in IMPSEC.IMP and CUSSEC.IMP. |
| Sequence | This indicates the sequence in which the entries are defined in the IMP files. |
| Column | Description |
|---|---|
| Description | This indicates the field name. |
| E.Net | This indicates whether the field is applicable for a business object for e.net. |
| Custom | This indicates whether the field is a third party custom program. |
| Company | This indicates the company. |
| Number | This indicates the activity number as defined in IMPSEC.IMP and CUSSEC.IMP. |
| Sequence | This indicates the sequence in which the entries are defined in the IMP files. |
This pane displays the operators, roles and groups that have access to the securables displayed in the Report Control pane.
The content displayed depends on the securable selected:
| Column | Content displayed |
|---|---|
|
System information |
|
|
Company information |
|
|
Program access |
|
|
Activities |
|
|
Fields |
|
|
Access Control |
|
|
Electronic signatures |
|
| Column | Description |
|---|---|
| Operator | This indicates the operator code. |
| Name | This indicates the operator name. |
| Primary role | This indicates the primary role of the operator. |
| Primary group | This indicates the primary group of the operator. |
| Administrator | This indicates whether the operator's primary group is an administrative group. |
| Configuration | This indicates how the operator's access is defined (e.g. by role). |
| Alternate roles |
If the operator has multiple roles then this column displays a comma-separated list of the alternate roles. |
| Analytics admin | This indicates whether the operator is flagged as an Analytics administrator. |
| Browse only |
This indicates whether the operator is only allowed browse access to a program (only relevant when viewing program access). |
| CMS only | This indicates if the operator is a contact management user only. |
| Conflicts |
If the operator has access to programs which are in conflict with the one selected, then this column indicates a list of the programs which may be in conflict (only relevant when viewing program access). |
| Espresso | This indicates if the operator is an Espresso user. |
| Job logging |
This indicates if job logging is required (only relevant when viewing program access). |
| Last login | This indicates the operator's last login date and time. |
| Locked | This indicates whether the operator's account has been locked. |
| POS only | This indicates whether this is a POS-only user. |
| Password expiry | This indicates whether the operator's password has an expiry date. |
| Password reqd | This indicates whether the operator has a password defined. |
| Report designer | This indicates whether the operator is allowed to design reports. |
| Role 2 - 5 | This indicates the name of alternate roles defined for the operator. |
| Role Designer | This indicates whether if the operator is allowed to design roles. |
| Subgroups | If subgroups are defined for the operator, then this column displays a comma-separated list of those sub groups. |
| Column | Description |
|---|---|
| Role and operator |
This indicates the role name. All associated operators to that role are displayed. |
| Operator | This indicates the operator code. |
| Primary role | This indicates the primary role defined for the operator. |
| Roles 2 – 5 | This indicates the secondary roles defined for the operator. |
| Access control | This indicates whether access control is set against the role. |
| Activities and fields | This indicates whether activity and field access is configured against the role. |
| Program access | This indicates whether program access is configured against the role. |
| Role code | This indicates the role code in the role table. |
| User interface | This indicates whether the option to maintain the user interface is defined for the role. |
| Workflow | This indicates whether Workflow is configured for the role. |
| eSignatures | This indicates whether electronic signatures are defined against the role. |
| Column | Description |
|---|---|
| Group and operator |
This indicates the group name. All operators associated with that group are displayed below. |
| Operator | This indicates the operator code. |
| Primary group | This indicates the primary group defined against the operator. |
| Subgroups | This indicates a comma-separated list of any subgroups defined against the operator. |
| Administrator | This indicates whether the group is defined an administrator group. |
| Group code | This indicates the group code. |
| Logout users | This indicates whether the group can log out users. |